Manage Information Security, Regulatory Compliance and Technology-Focused Business Continuity and Disaster Recovery
The protection of the confidentiality, integrity and availability of the IT environment, sensitive information, intellectual and educational assets, research data and institutional operations is a fundamental responsibility of the university. Disaster preparedness is a must for the continuity of operations and functions of the university if disaster strikes.
We must work together to promote a strong and secure infrastructure and excellent practices to protect that infrastructure. Developing and deploying appropriate policies and effective enforcement means to secure the integrity of information technology resources, safeguard institutional information and protect the privacy of university community members as they engage in online activities.
Success Stories
For clinical and translational research involving sensitive human subjects research data, the RCCI and Information Security Office (ISO) teams deployed more than 300 users in the Secure Research Environment (SRE) this year in support of the Institute for Computational Biology, the National Prion Disease Pathology Surveillance Center, the Begun Center for Violence Prevention Research and Education, the Center on Urban Poverty and Community Development and other research centers that use data requiring high levels of protection.
The SRE provides an isolated IT environment that permits our partner hospitals and clinical researchers to manage sensitive health data for research purposes, while addressing many of the confidentiality concerns that complicate medical research involving human subjects.
This milestone permits CWRU to pursue more clinical research projects with confidence that data availability for multiple researchers will permit greater discovery and continued research. growth.
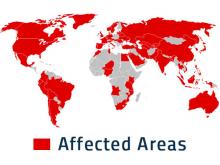
In May 2017, a global ransomware attack called "WannaCry" affected millions of users. Hospitals and industries running vulnerable Windows systems were particularly hit hard. Ransomware is a term used to describe malware that denies access to data or systems unless a ransom is paid to a cybercriminal.
Thanks to UTech’s earlier implementation of a network “Default Deny” policy and UTech’s rapid and coordinated response, the spread of the attack was minimized for CWRU. The server centralization initiative, which moved systems from the main campus network to CWRU data centers, helped defend against “WannaCry” because malicious attack patterns are isolated and blocked in the data centers. Finally, engineers were able to identify vulnerable systems and contact the appropriate users and administrators that needed support.
- presentations at the EDUCAUSE Security Professionals Conference
- Completed and published a Cloud Security Strategy, defining security goals and requirements for cloud services acquisition
- Completed the development of software integration of Duo Security with CWRU Single Sign-On, improving resilience of authentication systems from social engineering attacks and password theft
- Contributed to the cyber-security community in monthly meetings with peer colleagues from local industry and service businesses via membership in the Northeast Ohio CyberConsortium
- Created a Business Continuity Plan (BCP) for core IT systems, synchronizing security team responsibilities with existing disaster recovery plans and university Emergency Management Plans
- Refined the Security Risk Management Plan by adding scheduled security assessments of research and core business areas